**EDIT
Guys, this is 202x. We don't have sysadmins any more. Unless you're a hobbyist who is curious about the past, use something recent. There are loads to choose from. We went Google. But there's also Amazon, iCloud and maybe IBM have something...
UPDATE
Introducing s4bind: an alternative to Winbind. Simple and lightweight single sign on Active Directory for Linux and Windows. Details HERE
Aim
To provide a choice. Linux or Windows workstation. Same login. Same files. Different price.
Introduction
There's no doubt about it, introducing Linux boosts productivity. When it comes to workstations, Linux desktops have a distinct advantage. A customised GUI distinguishes your company from the predictable monotony of your competitors. More, you can have it now. Relieve your enterprise of the dated looking Microsoft and impossible to configure Mac interfaces. Give your employees something which looks up to date, is easy on the eye, simple to work with and which has your company ethos written deep into its underlying structure. Where would you rather work?
 |
| Ready for work. One of our Linux Clients |
 |
| Firmly back to the 90's with Windows |
Implement Active Directory, without the burden of Microsoft licencing. We'll create an example user called steve6, a group called suseusers and a shared folder for all members of suseusers called dropbox. Samba4 will be the boss. On the Linux side, we bypass winbind and cifs in favour of the lightening fast and all new nss-ldapd with an nfs4 fileserver
Warning
This is the quickstart version. If it's 3 am and Samba4 is still complaining about DNS, go here, You did install Samba4 according to the Samba4 how-to didn't you?
The Hard and Soft of it
Samba 4 PDC and NFS server: openSUSE 12.1
IP 192.168.1.3, fqdn hh3.hh3.site, hostname hh3
Linux Client: openSUSE 12.1
dhcp, hostname hh6
Windows Client Windows 7 Ultimate
dhcp, hostname steve-pc
 |
| The test domain: CACTUS |
/usr/local/samba/sbin/provision --realm=hh3.site --domain=CACTUS --adminpass=Myp@s1Wd --server-role=dc
Server
Edit /usr/local/samba/etc/smb.conf
[global]
server role = domain controller
workgroup = CACTUS
realm = site
netbios name = HH3
passdb backend = samba4
template shell = /bin/bash
[netlogon]
path = /usr/local/samba/var/locks/sysvol/hh3.site/scripts
read only = No
[sysvol]
path = /usr/local/samba/var/locks/sysvol
read only = No
[home]
path = /home/CACTUS
read only = No
[profiles]
path = /home/CACTUS/profiles/
read only = No
[dropbox]
path = /home/CACTUS/dropbox
read only = No
create mask = 0770
Set your path e.g. in /etc/environment
PATH="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/samba/bin:/usr/local/samba/sbin"
samba -i -d 3
Grab another root shell.
Turn off nscd:
$rcnscd stop
Create some users, groups and folders:
$samba-tool user add nslcd-service
$samba-tool user setexpiry nslcd-service --noexpiry
$samba-tool user add nfs-user
$samba-tool user setexpiry nfs-user --noexpiry
$groupadd nslcd-user
$useradd -s /bin/false -d /var/lib/nobody -g nslcd-user nslcd-user
$mkdir -p /home/CACTUS/profiles
$chmod 1777 /home/CACTUS/profiles
Install the package nss_pam_ldapd and then:
$chown nslcd-user:nslcd-user /etc/nslcd.conf
nslcd takes all the guesswork out of AD mapping. I only had to change 3 maps:
Edit /etc/nslcd.conf
uid nslcd-user
gid nslcd-user
uri ldap://hh3.site
base dc=hh3,dc=site
map passwd uid samAccountName
map passwd homeDirectory unixHomeDirectory
map group uniqueMember member
sasl_mech GSSAPI
sasl_realm HH3.SITE
krb5_ccname /tmp/nslcd.tkt
Make it readable by the nslcd-user:
chown nslcd-user:nslcd-user /etc/nslcd.conf
We get the mappings from ldap, so we need to tell nss in /etc/nsswitch.conf
passwd: files ldap
group: files ldap
Extract the key for nslcd-service:
$samba-tool domain exportkeytab /etc/nslcd.keytab --principal=nslcd-service
Grab k5start from here. Copy it to /usr/local/sbin and chmod + x it.
Start it:
$k5start -v -f /etc/nslcd.keytab -U -o nslcd-user -K 360 -k /tmp/nslcd.tkt &
Start nslcd:
$rcnslcd start
Next, we'll make s4 able to talk to Linux users and groups. This is a very basic mapping. For a full list of Linux user, group and start up scripts for Samba4, please see here.
We create and posix-ify a group called suseusers. Copy and paste this file as s4group and chmod + x it:
Copy from here --->
#!/bin/sh
echo "Creating s4 posix group "$1
samba-tool group add $1
strgid=$(wbinfo --group-info=$1)
gid=$(echo $strgid | cut -d ":" -f 3)
echo "dn: cn=$1,cn=Users,dc=hh3,dc=sit
changetype: modify
add:objectclass
objectclass: posixGroup
-
add: gidnumber
gidnumber: $gid" > /tmp/$1
ldapmodify -h 192.168.1.3 -D cn=Administrator,cn=Users,dc=hh3,dc=site -f /tmp/$1 -Y GSSAPI
rm /tmp/$1
echo $1 "posix-ified"
<--- to here
Then, tickets please:
kinit Administrator
and create the group:
./s4group suseusers
Now we make the dropbox share and set permissions for our suseusers group:
mkdir -m 1770 /home/CACTUS/dropbox
chown root:suseusers /home/CACTUS/dropbox
chmod g+s /home/CACTUS/dropbox
setfacl -d -m g::rw /home/CACTUS/dropbox
This sets files created in the dropbox folder editable by everyone in suseusers. If you want directories created to be group rw too:
setfacl -d -Rm g::rwx /home/CACTUS/dropbox
For full details of the share please go here.
Now we'll create a user steve6, posix-ify him and put him in the suseusers group.
Here is a script to do that for us. Similar idea to the group script. We'll call this one s4user:
Copy from here -->
#!/bin/bash
echo "Creating s4 posix user "$1
echo "Pls enter pwd for "$1
samba-tool user add $1
sleep 2
#get the uid
struid=$(wbinfo -i $1)
uid=$(echo $struid | cut -d ":" -f 3)
#get the gid
strgid=$(wbinfo --group-info=$2)
gid=$(echo $strgid | cut -d ":" -f 3)
#get the group from the sid
strsid=$(wbinfo --gid-to-sid=$gid)
primarygid=$(echo $strsid | cut -d "-" -f 8)
strwg=$(echo $struid | cut -d "\\" -f 1)
#add the posix attributes to the user
echo "dn: CN=$1,CN=Users,DC=hh3,DC=site
changetype: modify
add: objectclass
objectclass: posixaccount
-
add: uidnumber
uidnumber: $uid
-
add: gidnumber
gidnumber: $gid
-
add:unixhomedirectory
unixhomedirectory: /home/$strwg/$1
-
add: loginshell
loginshell: /bin/bash" > /tmp/$1
ldbmodify --url=/usr/local/samba/private/sam.ldb -b dc=hh3,dc=site /tmp/$1
samba-tool group addmembers $2 $1
#set the user to the posix group
echo "dn: CN=$1,CN=Users,DC=hh3,DC=site
changetype: modify
replace: primarygroupid
primarygroupid: $primarygid" > /tmp/$1
echo "sleeping. . ."
sleep 5
ldbmodify --url=/usr/local/samba/private/sam.ldb -b dc=hh3,dc=site /tmp/$1
mkdir /home/$strwg/$1
chown -R $1:$2 /home/$strwg/$1
rm /tmp/$1
hostname=$(hostname -s)
echo "dn: CN=$1,CN=Users,DC=hh3,DC=site
changetype: modify
add: profilePath
profilePath: \\\\$hostname\\profiles\\$1
-
add: homeDrive
homeDrive: Z:
-
add: homeDirectory
homeDirectory: \\\\$hostname\\home\\$1" > /tmp/$1
echo "sleeping. . ."
sleep 5
ldbmodify --url=/usr/local/samba/private/sam.ldb -b dc=hh3,dc=site /tmp/$1
echo "New user: " $1 "POSIX-ified as follows:"
echo "uid " $uid
echo "gid " $gid
echo "primaryGroupID " $primarygid " :$2"
echo "getent passwd $1"
echo $(getent passwd $1)
echo "sid " $(wbinfo --gid-to-sid=$gid)
db=/usr/local/samba/private/sam.ldb
ldbsearch --url=$db cn=$1 | grep \\\\$hostname
ldbsearch --url=$db cn=$1 | grep homeDrive
rm /tmp/$1
<-- to here and chmod +x it.
Don't know why we can't do the ldbmodify in a single step. I tried, but no go. Some error about ERR: (Unwilling to perform) LDAP error 53. Anyway, it works OK like this.
Then create steve6:
./s4user steve6 suseusers
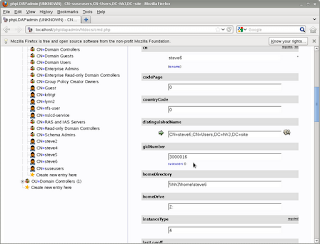
Of course, you could do the user and group stuff with phpldapadmin too:
 |
| The point and click method, 2 |
Next we configure nfs4 by installing the nfs server. Use Yast to install the nfs-server. Create a service principal for nfs and extract the key:
$samba-tool spn add nfs/hh3.hh3.site nfs-user
$samba-tool domain exportkeytab /etc/krb5.keytab --principal=nfs/hh3.hh3.site
gss expects to find some sort of machine identifier in the keytab, so we also need:$samba-tool domain exportkeytab /etc/krb5.keytab --principal=HH3$
/home 192.168.1.0/24(rw,sec=none:sys:krb5:krb5i:krb5p,no_subtree_check,insecure)
 |
| If you're happy with the limitations of nfs4 acl's Yast NFS module for kerberized nfs4 |
 |
| If you want your acl's to work as you expect Yast NFS module for Kerberized nfs3 |
rpc.idmapd -fvvv
Warning: do not edit /etc/resolv.conf. Use Yast Network Settings to point at 192.168.1.3 and start the domain search at hh3.site:
 |
| Set your hostname to hh6, not hh3 |
192.168.1.3 hh3.hh3.site hh3
127.0.1.1 hh6.hh3.site hh6
to /etc/hosts127.0.1.1 hh6.hh3.site hh6
Go no further until you can ping the server on both name and IP, and hostname -f gives hh6.hh3.site.
Configure Kerberos. Guess what I used:
 |
| More Yast time saving |
It will pull in the other Kerberos stuff you need too. The Samba4 provision should have created a krb5.con for you:
An easy way to get the rest of Kerberos is to join the domain. Install samba-client and create /etc/samba/smb.conf as follows:
[libdefaults]
default_realm = HH3.SITE
dns_lookup_realm = false
dns_lookup_kdc = true
You can use the one that Yast created or the Samba4 one in case of problem later on.
workgroup = CACTUS
realm = HH3.SITE
security = ADS
Now join the hh3.site domain (fingers crossed):
$net ads join -U Administrator
kerberos method = system keytab
to smb.conf and create the host and machine keys for the client:
$net ads keytab create -U Administrator
We now bypass winbind by installing the package nss_pam_ldapd
Use a USB pendtive, 5 1/4" floppy disk or punched cards to transfer the following files and applications:
/etc/nslcd.conf
/etc/nslcd.keytab
/usr/local/sbin/k5start
/etc/nslcd.keytab
/usr/local/sbin/k5start
from the server to the respective locations on the client.
Start k5start:
$k5start -f /etc/nslcd.keytab -U -o nslcd-user -K 360 -k /tmp/nslcd.tkt &
Edit /etc/idmapd.conf
[General]
Verbosity=0
Pipefs-Directory=/var/lib/nfs/rpc_pipefs
Domain=hh3.site
[Mapping]
Nobody-User=nobody
Nobody-Group=nobody
Start nslcd:
rcnslcd start
USE_KERNEL_NFSD_NUMBER="4"
MOUNTD_PORT=""
NFS_SECURITY_GSS="yes"
NFS3_SERVER_SUPPORT="yes"
NFS4_SUPPORT="yes"
SM_NOTIFY_OPTIONS=""
NFS_START_SERVICES="yes"
STATD_OPTIONS=""
NFSV4LEASETIME=""
RPC_PIPEFS_DIR=""
SVCGSSD_OPTIONS=""
NFSD_OPTIONS=""
Or use Yast:
 |
| Select nfs4 and set the domain for idmapd.conf |
 |
| Runlevels. Setting the nfs client services to start at boot |
OpenSUSE sometimes starts the gss daemon, so you either need to start it manually:
rpc.gssd
. . .or, perhaps better for now so we can see when it doesn't mount, open two more shells:
shell 1:
$rpc.gssd -fvvv
shell 2:
$rpc.idmapd -fvvv
Finally, root gets us ready for work:
nfs4:
$mount -t nfs4 hh3:/home /home -o sec=krb5
nfs3:
$mount -t nfs hh3:/home /home -o vers=3,sec=krb5
Windows client
As local Admin, set 192.168.1.3 as your only DNS.
 |
| The beautifully designed windows network settings dialogue |
Set the date and time to match exactly that on the server. Add two registry entries to look like this:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanManWorkstation\Parameters
 |
| DNSNameResolutionRequired 0 |
 |
| DomainCompatibilityMode 1 |
 |
| Joining the domain. This is quite scary. Forgot to do a screenshot. This is on another client called SuSE-pc. Sorry. |
Then, in true Microsoft style, reboot.
At the login screen, hit ctrl+alt+del (or right-shift+del if like here, you're on virtualbox). You'll see the offer to log onto the CACTUS domain. Accept the offer. Logon as Administrator.
Download the Microsoft remote tools here and choose to install anything that mentions AD. Warning, it takes ages. We've prepared howto's for how to join a domain and setup the remote tools for both XP and win7.
Then, Control panel > Programs and Features > Turn windows features on or off > Remote Server Administration Tools > Administration Tools > Choose AD DS and AD LDS Tools > OK
If you're the sort of user that likes clicking something on a menu, then continue by choosing Administrative Tools from the program menu then select AD options. Otherwise at the bottom of start menu type run then click on the word 'run' which appears above where you typed 'run' beforehand, then type the self explanatory name of dsa.msc in the window called 'run'. As you are now a windows user, I am also obliged to tell you to click on 'OK'after you have typed dsa.msc
 |
| Describing our new group |
 |
| the whole proof |
 |
| Checking profile and home folders for steve6 |
Our script has already done this for us. You can change it here if you wish. (Don't). Enter \\hh3\profiles\steve6 in the profile field at the top and map Z: to \\hh3\home\steve6 fields at the bottom. Log out and back in to CACTUS, this time as steve6. In explorer type Z:\ or \\hh3 in explorer. You'll see your Linux files. I'll stick this stuff in the s4user script later.
Check the primary group for steve6:
 |
| Setting the default group. Note the POSIX message. |
 |
| steve6 on the Windows client |
Setting up the dropbox share
As this is not crucial at the moment and for fear of being too lengthy, we documented setting up the dropbox share in this post instead of boring you here. acls turned out to be quite entertaining.
Testing
Server:
hh3:/home/steve # getent passwd steve6
steve6:*:3000015:3000016:steve6:/home/CACTUS/steve6:/bin/bash
hh3:/home/steve # getent group suseusers
suseusers:*:3000016:
hh3:/home/steve # wbinfo -i steve6
CACTUS\steve6:*:3000015:3000016::/home/CACTUS/steve6:/bin/false
hh3:/tmp # id steve6
uid=3000015(steve6) gid=3000016(suseusers) groups=3000016(suseusers)
Client:
steve6@hh6:~> id
uid=3000015(steve6) gid=3000016(suseusers) groups=3000016(suseusers)
steve6@hh6:~> echo "Hola" > file
steve6@hh6:~> ls -l file
-rw-r--r-- 1 steve6 suseusers 5 Feb 9 13:52 file
 |
| steve6 on xfce |
 |
| steve6 on KDE |
Client and server
If you're not in a hurry, why not try cifs?
 |
| CLIENT: The call to the fileserver In this case it was steve4@192.168.1.10 |
 |
| SERVER: authentication cifs |
Or, for CLI freaks:
$smbclient //hh3/home -U steve6
Enter password for steve6.
smb:\>
exit
Testing the user and group scripts
Here is a new user steve8 being added to the suseusers group:
hh3:/tmp # s4user steve8 suseusers
Creating s4 posix user steve8
Pls enter pwd for steve8
New Password:
User 'steve8' created successfully
Modified 1 records with 0 failures
Added members to group suseusers
sleeping. . .
Modified 1 records with 0 failures
sleeping. . .
Modified 1 records with 0 failures
New user: steve8 POSIX-ified as follows:
uid 3000033
gid 3000020
primaryGroupID 1118 :suseusers
getent passwd steve8
steve8:*:3000032:3000020:steve8:/home/CACTUS/steve8:/bin/bash
sid S-1-5-21-443838659-2890314986-1722269781-1118
profilePath: \\hh3\profiles\steve8
homeDirectory: \\hh3\home\steve8
homeDrive: Z:
Bugs
ldbmodify? rpc.gssd?
Conclusion
The ideal setup for casual home use. Perfect for gaming and writing brief e-mail messages.
Stuck? How do I do it on Ubuntu? Questions? More screenshots?
Drop a line and I'll do my best. There's also the samba mailing list.